In today’s digital threat landscape, domain spoofing and phishing remain top attack vectors. As a security-focused organization, SCM360 recently experienced an attempted phishing attack impersonating our domain. This case study explains how we detected the attack, verified our email security gaps, and implemented SPF, DKIM, and DMARC to harden our domain against future abuse.
📌 Real Attack Scenario: Spoofed “Admin” Alert
On May 27, 2025, our support@scm360.co.uk inbox received a suspicious email titled "Incoming Mails On Hold", appearing to come from admin@scm360.co.uk.
- Spoofed display name and domain
- Misleading subject to create urgency
- Fake internal notification style
- Time format inconsistency (AM/PM vs system 24hr logs)
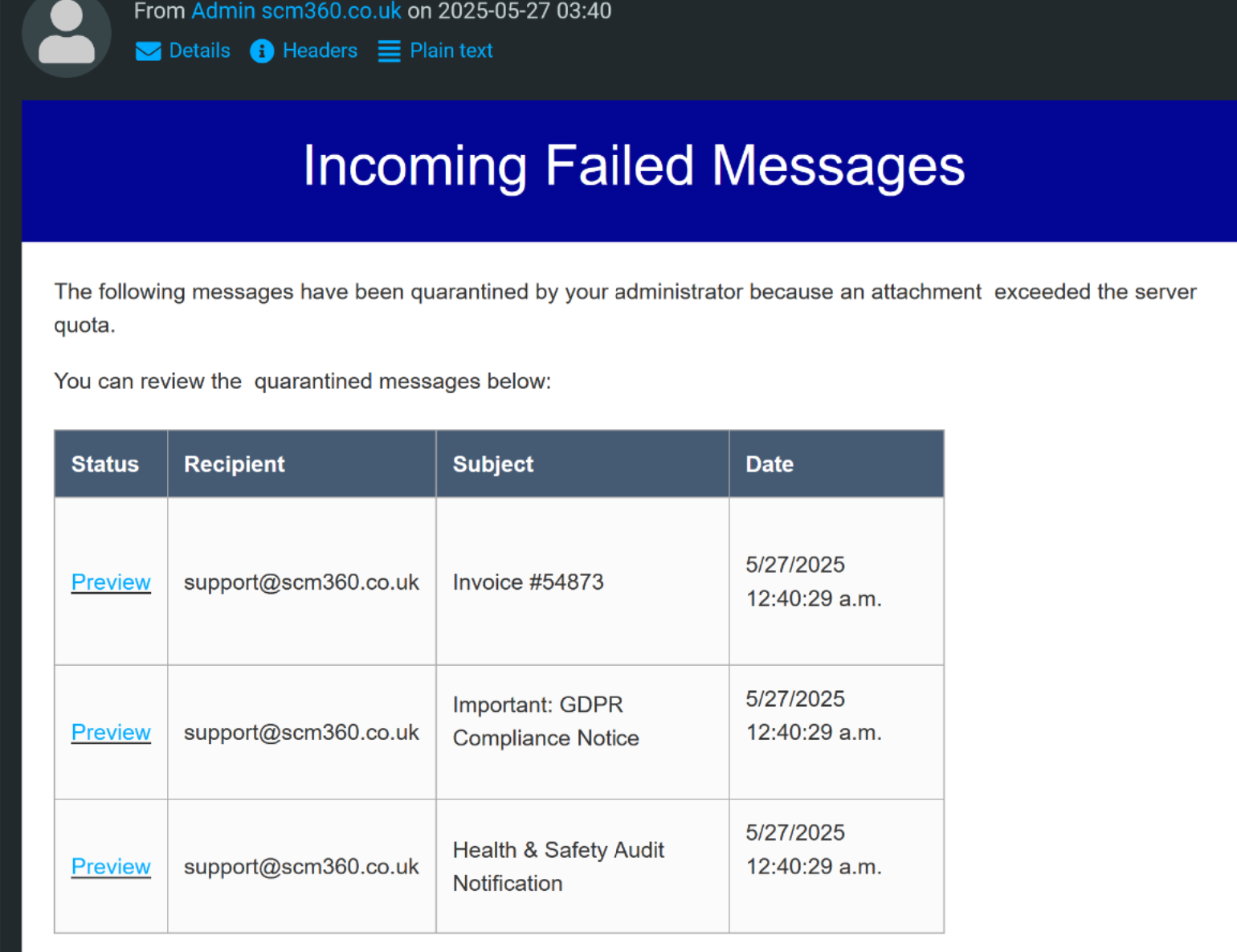
🧪 Diagnostic Step: Header Analysis & Port25 Test
We tested our domain using Port25 Email Authentication Verifier. The response confirmed SPF, DKIM, and iprev passed. However, our DMARC policy was set to p=none, meaning spoofed emails weren’t being rejected or quarantined.
🔧 Technical Fixes Applied
✅ SPF (Sender Policy Framework)
We verified only trusted outbound mail servers are allowed:
v=spf1 include:relay.mailbaby.net ~allWe plan to move to -all after monitoring.
✅ DKIM (DomainKeys Identified Mail)
Enabled via our provider:
default._domainkey.scm360.co.uk IN TXT "v=DKIM1; k=rsa; p=MIIBIjANBgkq..."✅ DMARC (Domain-based Message Authentication, Reporting & Conformance)
Started with a monitoring policy:
_dmarc.scm360.co.uk IN TXT "v=DMARC1; p=none; rua=mailto:postmaster@[ourdomain]"Plan: move to p=quarantine and then p=reject.
🔍 Results
- ✅ SPF: PASS
- ✅ DKIM: PASS
- ✅ DMARC: Live monitoring via aggregated reports
- ✅ Spoofing attempts now flagged or rejected
🧠 Lessons & Recommendations
- Always start with SPF — immediate impact.
- Enable DKIM — especially if using hosted mail services.
- Implement DMARC — even in monitoring mode.
- Use Port25, MXToolbox, or dmarcian.com for testing.
📣 Disclaimer
This article includes real DNS configurations used by SCM360 for educational purposes. Sensitive parts like full DKIM keys and internal addresses have been masked. Adjust records to your provider and domain infrastructure as needed.
👇 What’s Next?
We’re developing a Laravel-integrated DMARC dashboard with log insights. Interested in early access or collaboration?
Email: cyber@scm360.co.uk

